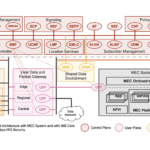
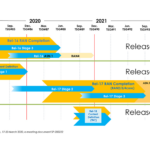
IoT Networks
IoT Wireless Protocols – Spreadsheet

IoT Wireless Protocols
| wdt_ID | Wireless technology / standard | Organization that manages the technology / standard | URL of the organization | URL of the standard specification | Frequency | Approximate Range | Data Rate | Power Draw | Topology | Requires hub or gateway | Proprietary or Open | Intended Use | Security | Common use | Comments |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 5G | 3GPP | https://www.3gpp.org/ | https://www.3gpp.org/dynareport/SpecList.htm?release=Rel-15&tech=4 | Low-band 5G 600 - 700 MHz /Mid-band 5G 2.5-3.7 GHz / High-band 5G 25 - 39 GHz and higher frequencies up to 80GHz | Range is correlated with frequency bands - low band 5G has similar range to 4G (tens of kilometers), Mid-band 5G has several km range. High-band 5G has hundreds of meters up to 1.5 km range. | Low-band 5G (600 - 700 MHz) giving download speeds a little higher than 4G at the moment: 30-250 Mbps. Mid-band 5G (2.5-3.7 GHz) currently allowing speeds of 100-900 Mbps. High-band 5G (25 - 39 GHz and higher frequencies up to 80GHz) achieves, at the mom | Low | Star | No | Open | Personal, Single building, Campus, LAN, Software defined WAN (SD WAN) | Encryption is evolved from 4G. It is more complex and based on multi-layer & multi-criteria approach. Generally, the level of 5G security is not defined by the number of specified security mechanisms. A multi-stakeholder approach that involves operator | Expectations are that 5G will expand boundaries in all domains of modern life such as travelling, driving, production efficiency improvements, smart systems deployment such as smart cities with smart homes, buildings, hospitals, factories, public safety, | The first phase of 5G specifications is defined in 3GPP Release 15. 5G is equipped with new air interface that supports heterogeneous access networks and handles variable bandwidths. Packet core network upgrades are also implemented, where traditional and |
| 2 | ANT+ Alliance | Garmin | http://www.garmin.com/en-US | https://www.thisisant.com/ | 2.4GHz | ≈ 30m | 12.8 Kbit/s - 60kbit/s | Low | Peer to peer, Star, Mesh, broadcast, ANT - FS, shared cluster. | Yes | Open | Single Building | ANT supports an 8-byte (64-bit) network key and 128-bit AES encryption for ANT master and slave channels. If further security is required, authentication and encryption can be implemented through the application level. ANT devices may use the public net | ANT in residential, commercial and industrial sensing, control applications. ANT + predominantly in health and wellness - blood pressure monitoring, fitness, cycling, running, continuous glucose monitoring, emergency response alerts, audio control, hear | ANT is a purpose-built ultra-low-power wireless networking protocol operating at 2.4GHz. ANT+ is an implementation of ANT and is an ecosystem of interoperable products built on device profiles. ANT devices may use any RF frequency from 2400MHz to 2524MHz |
| 3 | Bluetooth | Bluetooth SIG, Inc. | https://www.bluetooth.com/ | https://www.bluetooth.com/specifications/ http://www.bluetooth.org/docman/handlers/DownloadDoc.ashx?doc_id=40560 | 2.4GHz | ≈ 50m | ≈ 2Mbps | Medium | Scatternet | Yes | Open | Single building | Several security modes are recognized in Bluetooth technology, and generally each version of Bluetooth standard supports some of them. These modes are mutually different according to the point of security initiation in Bluetooth devices. Bluetooth devices | Bluetooth technology is used for data streaming or file exchange between mobile phones, PCs, printers, headsets, joysticks, mice, keyboards, stereo audio or in the automotive industry. | Bluetooth is wireless communications technology based on the IEEE 802.15.1 protocol. Bluetooth technology is supported by 1 master & up to 7 slave nodes, while the number of slave nodes is not limited by specification in BLE networks. In the most recent |
| 4 | BLE (Bluetooth Low Energy) or Bluetooth Smart (Bluetooth 5, 4.2) | Bluetooth SIG, Inc. | https://www.bluetooth.com/ | https://www.bluetooth.org/DocMan/handlers/DownloadDoc.ashx?doc_id=421043 | 2.4GHz | ≈ 100m | <1Mbps ≈ (n x 100kbps) | Low | Scatternet | Yes | Open | Single building | In compliance with the Bluetooth Specification Version 5.0, two Security modes are implemented in BLE: Security mode 1 and Security mode 2. BLE security mode 1 has 4 layers: 1) No security (without authentication and without encryption). 2) Unauthenticat | BLE technology is nowadays an indispensable part of mobile phones, PCs and other types of devices applicable in gaming, sports, wellness, industrial, medical, home and automation electronics. BLE provides wireless connectivity that enables home automatio | It is important to notice that Bluetooth and BLE are not compatible technologies. For example, channel bandwidth in Bluetooth technology is 1MHz and in BLE is 2MHz, number of channels in Bluetooth is 79, while BLE is supported by 40 channels. Moreover, th |
| 5 | GSM/GPRS/EDGE (2G), UMTS/HSPA (3G), LTE (4G) | 3GPP | https://www.3gpp.org/ | https://www.3gpp.org/specifications/releases | 700/800/8508900/1800/1900/2100/2300/2500/2600MHz | ≈ 35km max for GSM and ≈ 200km max for HSPA | Typical download: 35-170kps (GPRS), 120-384kbps (EDGE), 384Kbps-2Mbps (UMTS), 600kbps-10Mbps (HSPA), 3-10Mbps (LTE) | High | Cellular | No | Open | Personal, Single building, Campus, | Authentication algorithms were not very strong in 2G networks and were based on master security key . In 3G wireless standard (3GPP based) , the authentication mechanism was enhanced to become a two-way process. In addition, 128-bit encryption and integri | 2G offered digital communications. 3G has been generic data cellular mobile technology that provided broadband transmissions. 4G is the first all IP cellular data communication technology with dominant data transfer services and IoT support capabilitie | Expectations are that the IoT ecosystem and its evolution support will be the most important criteria for further development of cellular mobile technologies. |
| 6 | IEEE 802.15.4 | IEEE | https://www.ieee.org// | https://standards.ieee.org/standard/802_15_4s-2018.html | 2.4GHz | ≈ 100m | ≈ 20 kbps and 40 kbps (BPSK ), ≈ 250 kbps (O-QPSK with DSSS) | Low | Star, Mesh, peer-to-peer | Yes | Open | Single Building | The IEEE 802.15.4 standard protects information at the Medium Access Control (MAC) sublayer of the OSI Reference Model. The implemented cryptographic mechanism in this standard is based on the symmetric-key cryptography and uses keys that are provided by | Typical use cases are smart homes and buildings i.e. home security, lighting control, air conditioning and heating systems; industrial automation; automotive sensing; education; consumer electronic devices and personal computer accessories. | The IEEE 802.15.4 standard defines the interconnection protocol for the low-rate wireless personal area networks (LR-WPANs). This standard provides short range wireless communications between battery - powered nodes. The power consumption in IEEE 802.15. |
| 7 | ISA100.11a | ISA | https://www.isa.org | https://www.isa.org/pdfs/2008-seminar/ISA100_Overview_Oct_2008/ | 2.4 GHz | ≈ 100m | ≈ 250 kbps | Low | Star, Mesh | Yes | Proprietary | Single Building | ISA 100.11a standard is embedded with integrity checks and optional encryption at data link layer of the OSI reference model. Moreover, security mechanisms are provided in transport layer. too. 128 bits keys are used in both transport and data link layers | The most important use cases are reliable monitoring and alerting, asset management, predictive maintenance and condition monitoring, open - loop control and closed loop control industrial applications. | ISA 100.11a low data rate connectivity is supported with increased security and system management levels. In compliance with best practices, optimal number of nodes in the network is 50-100. |
| 8 | 6LoWPAN | IETF | https://www.ietf.org/ | https://tools.ietf.org/html/rfc8138 | 2.4 GHz | ≈ 100m | ≈ 250 kbps | Low | Mesh | Yes | Open | Single Building | 6LoWPAN has implemented AES-128 link layer security - which is defined in IEEE 802.15.4 protocol. This security mechanism provides link authentication and encryption. Additional security features are enabled by the transport layer security mechanisms ove | There are many applications where 6LoWPAN is being used: automation, industrial monitoring, smart grids (enable smart meters and other devices to build a micro mesh network), smart homes and smart buildings. | 6LoWPAN (IPv6 over Low-Power Wireless Personal Area Networks), is a low power wireless mesh network. It is specified in IETF standard RFC 8138. Every node in the 6LoWPAN network is embedded with its own IPv6 address. This allows the node (typically sensor |
| 9 | LoRaWAN | LoRa Alliance | https://www.lora-alliance.org | https://lora-alliance.org/resource-hub/lorawanr-specification-v11 | 433 MHz, 868 MHz (Europe), 915 MHz (Australia and North America) and 923 MHz (Asia) | ≈ 15km | ≈ 0.3-50 kbps | Low | Star of Stars | Yes | Open | WAN | The fundamental properties that are supported in LoRaWAN security are mutual authentication, integrity protection and confidentiality. Mutual authentication is established between a LoRaWAN end-device and the LoRaWAN network as part of the network join p | Some representative LoRaWAN use cases are smart homes and buildings, smart city applications and utility companies , smart metering, agriculture, civil infrastructures and industrial facilities as well. | LoRaWAN is a Low Power Wide Area Network (LPWAN) technology. It provides wireless, low-cost and secure bi-directional communication for Internet of Things (IoT) applications. LoRaWAN is optimized for long range communication, low power consumption and is |
| 10 | EC-GSM-IoT | 3GPP / GSMA | https://www.3gpp.org/ | http://www.gsma.com/iot/extended-coverage-gsm-internet-of-things-ec-gsm-iot/ | 850-900 MHz (GSM bands) | ≈ 15km | 70 kbps (GSMK), 240 kbps (8PSK) | Low | Star | No | Proprietary - The EC-GSM- IoT Group is Open to GSMA Members and Associate Members, however all members must positively contribute to the Group's high-level objectives, including promoting EC-GSM- IoT technology and encouraging new service and applicati | WAN | The EC-GSM-IoT has improved security, compared to the existing GSM/GPRS networks - offers integrity protection, mutual authentication and implements stronger ciphering algorithms. | Battery life of up to 10 years can be supported for a wide range of use cases. Coverage extension beyond GSM enables coverage of challenging indoor and outdoor locations or remote areas in which sensors are deployed for agriculture or infrastructure monit | Extended coverage GSM IoT (EC-GSM-IoT) is a standard-based Low Power Wide Area technology specified by 3GPP Rel. 13. It is based on eGPRS and designed as a high capacity, long range, low energy and low complexity cellular system for IoT communications. Th |
| 11 | LTE-MTC Cat 0 | 3GPP | https://www.3gpp.org/ | https://www.3gpp.org/ftp/Information/WORK_PLAN/Description_Releases/ | LTE technology frequency bands are used LTE-MTC Cat 0 (700MHz, 800 MHz, 900MHz, 1700MHz, 1800MHz, 1900MHz, 2300MHz, 2400MHz, 2500MHz, 2700MHz). | Range is variable and depends on frequency bands, propagation conditions etc. typically it is ≈ 10km | ≈ 1 Mbps | Low | Star | No | Open | WAN | System and security management is more complex in LTE-MTC compared to LTE, as there are massive numbers of devices in LTE MTC network. At the same time, the request defined in 3GPP TS 22.368 is "LTE MTC optimizations shall not degrade security compared | LTE MTC can be applicable to various use cases including industrial automation and control, intelligent transportation, automatic meter reading, smart electricity distribution and management, smart homes/offices/shops, smart lighting, smart industrial pla | LTE-MTC Cat 0 (LTE machine type communications) is determined in 3GPP Rel. 12 specification. |
| 12 | LTE-M (Cat M1, Cat M2 ) - eMTC | 3GPP | https://www.3gpp.org/ | https://www.3gpp.org/ftp/Information/WORK_PLAN/Description_Releases/ | LTE technology frequency bands are used for LTE-M Cat M1 and Cat M2 (400MHz 450MHz, 600MHz, 700MHz, 800MHz, 900MHz, 1400MHz, 1500MHz, 1700MHz, 1800MHz, 1900MHz, 2100MHz, 2300MHz, 2400MHz, 2500MHz, 2600MHz, 2700 MHz). | Range is variable and depends on frequency bands, propagation conditions etc. typically it is ≈ 10km | LTE-M Cat M1 ≈ 1 Mbps LTE-M Cat M2 ≈ 4 Mbps DL / ≈ 7 Mbps UL | Low | Star | No | Open | WAN | LTE-M technology offers SIM-based security features requiring device authentication to connect to the network. Although it shares the LTE security standards, security system and management is more complex in LTE-M (eMTC) due to massive connectivity that | LTE M (eMTC) technology supports many use cases, like smart cities, smart agriculture, logistics and transportation, industry and manufacturing automation. | LTE-M Cat M1 is specified by 3GPP Rel.13 and LTE-M Cat M2 is specified by 3GPP Rel.14. Voice over LTE (VoLTE) is usable on LTE- eMTC communications. Two new features are enabled in eMTC, like extended Discontinuous Reception (eDRX), and Power Saving Mo |
| 13 | NB-IoT - Narrowband-IoT (LTE Cat NB1 and LTE Cat NB2) | 3GPP | https://www.3gpp.org/ | https://www.3gpp.org/ftp/Information/WORK_PLAN/Description_Releases/ https://www.3gpp.org/news-events/1785-nb_iot_complete | In-band LTE carrier, or within LTE guard bands, or standalone in re-farmed GSM spectrum - 700, 800 or 900 MHz. The 3GPP Release 14 introduced five new FDD frequency bands for NB-IoT: 11 (central frequencies - UL 1437.9 MHz, DL 1485.9 MHz), 21 (central | Range is variable and depends on frequency bands, propagation conditions etc. typically it is better than LTE-M coverage. | LTE Cat NB1 ≈ 66 kbps (multi-tone) and ≈ 16.9 Kbit/s (single-tone) LTE Cat NB2 ≈ 159kbps | Low | Star | No | Open | WAN | Multilayer security is applied in NB-IoT- network level and application level security, including support for user identity confidentiality, entity authentication, data integrity, and mobile device identification. | Some NB - IoT use cases are smart metering (electricity, gas and water), facility management services, security systems, connected personal appliances measuring health parameters tracking of persons, animals or objects, smart city and industrial appliance | NB-IoT is is determined in 3GPP Rel. 13 specification (LTE Cat NB1) and 3GPP Rel. 14 specification (LTE Cat NB2). NB-IoT has good indoor coverage and supports a massive number of low throughput end devices - sensors. It has low delay sensitivity, low d |
| 14 | Neul | Neul | http://www.neul.com/neul/ | http://www.neul.com/neul/ | 900MHz (ISM), 458MHz (UK), 470-790MHz (White Space) | ≈ 10km | up to 100kbps | Low | Star | Yes | Open | WAN | The wireless communications links between the gateway (base station) and the network nodes are encrypted. | The Neul communications technology is a wide-area wireless networking technology designed for the IoT and created to compete against existing cellular communications technologies solutions, applicable to smart metering, facility management services, se | Neul leverages very small slices of the TV White Space spectrum to deliver high scalability, high coverage, low power and low-cost wireless networks. Systems are based on the Iceni chip, which communicates using the white space radio to access the high-qu |
| 15 | NFC | NFC | http://nfc-forum.org/ | https://nfc-forum.org/our-work/specification-releases/specifications/nfc-forum-technical-specifications/ | 13.56MHz (ISM) | ≈ 10cm | 106kbps, 212kbps, 424kbps | Low | Point to point | No | Proprietary | Single Building | One of the security mechanisms implemented in NFC is Digital Signature (defined in the NFC Forum Signature RTD 2.0) with asymmetric key exchange [RD]. The Digital Signature is a part of the NFC Data Exchange Format (NDEF) message, which includes also a Ce | Some representative NFC use cases are ticket confirmation for sports events, concerts, at theaters, cinemas; welfare performances improvement - syncing workout data from a fitness machines with personal user device; personalized content sharing - viewing | NFC is a short range two-way wireless communication technology that enables simple and secure communication between electronic devices embedded with NFC microchip. There are three available modes of NFC communication: - Read/write (e.g. for reading tags i |
| 16 | RPMA (Random Phase Multiple Access) | Ingenu | https://www.ingenu.com/technology/rpma/ | https://www.ingenu.com/technology/rpma/how-rpma-works/ | 2.4 GHz | ≈ 70km | 100kb | Low | Star | Yes | Proprietary | WAN | Security in RPMA wireless technology is built on 128 b AES. It offers security features such as: mutual authentication, message integrity and replay protection, message confidentiality, device anonymity, authentic firmware upgrades and secure multicasts. | RPMA is applicable for many use cases such as asset tracking, agriculture, oil fields automation, environmental monitoring, smart city, fleet management and logistics, industrial automation, connected cars, etc. | Before IoT, Ingenu (previously OnRamp) was selling metering infrastructure that collected low power information from electricity meters. Ingenu has created random phase multiple access (RPMA), which uses Direct Sequence Spread Spectrum (DSSS) and is simil |
| 17 | IEEE 802.11a/b/g/n/ac | Wi-Fi Alliance | https://www.wi-fi.org/ | https://www.wi-fi.org/discover-wi-fi/specifications | 2.4GHZ/5GHz | ≈ 50m | Different data rates are enabled in IEEE 802.11 family of standards and their theoretical throughput is 11 Mbps ( IEEE 802.11b), 54 Mbps (IEEE 802.11a and IEEE 802.11g), 100 Mbps (IEEE 802.11n) or 300 Mbps (IEEE 802.11ac). | High | Star | No | Open | Single Building | The Wi-Fi Alliance enables the implementation of different security solutions across Wi-Fi networks through the Wi-Fi Protected Access (WPA) family of technologies. Simultaneously with Wi-Fi technology, deployable for personal and enterprise networks, sec | Typical Wi Fi use cases are use cases are audio/video streaming applications, centralized management applications, video monitoring ad security systems, etc. Networking of multiple devices such as cameras, lights and switches, monitors, sensors and many o | The Wi-Fi represents wireless technology that includes the IEEE 802.11 family of standards (IEEE 802.11a, IEEE 802.11b, IEEE 802.11g, IEEE 802.11n, IEEE 802.11ac, etc.). Within the 50m range, it operates in 2.4 GHz and 5GHz frequency bands. This technol |
| 18 | IEEE 802.11ah (Wi-Fi HaLow ) | IEEE | https://www.ieee.org | https://standards.ieee.org/standard/802_11ah-2016.html | 900MHz | ≈ 900m | 347Mbps | Low | Star | No | Open | Single Building, campus, WAN | Security is typically based on WPA 3 protocol with available personal and enterprise solutions. | Some representative IEEE 802.11ah use cases are health care, outdoor activities, smart metering, environmental sensing, home security, smart homes and buildings, power management, industrial automation, etc. | A Wi-Fi HaLow (IEEE 802.11ah) standard works at 900 MHz frequency band in the USA and significantly improves wireless coverage and energy efficiency as one of the most important features for IoT use cases. Wi-Fi HaLow devices have instant internet access |
| 19 | IEEE 802.16 (WiMax) | IEEE | https://www.ieee.org | http://wimaxforum.org/TechSpec | 2.3 GHz, 3.5 GHz, 5.8GHz | ≈ 50km | 40Mbit/s - mobile, 1 Gbit/s - fixed | High | PMP | No | Open | MAN | Different security solutions are enabled in WiMax networks, like Advanced Encryption Standard (AES) with 128-bit key: Rivest, Shamir and Adelman (RSA) with 1024-bit key and Triple Digital Encryption Standard (3-DES).Both Advanced Encryption Standard (AES) | WiMax applicability is recognized in wireless MAN deployment, provisioning of Internet connectivity and generic user applications, environmental monitoring, smart cities , telemedicine etc. | IEEE 802.16 technology has been put forward to overcome the drawbacks of WLANs and mobile networks. It provides different QoS scheduling for supporting heterogeneous traffic including legacy voice traffic, VoIP (Voice over IP), voice and video streams and |
| 20 | HART | HART Communication Foundation | https://fieldcommgroup.org/ | https://fieldcommgroup.org/technologies/hart/hart-technology-detail | 2.4 GHz | ≈ 200m | 250 kbps | Low | Star & Mesh | Yes | Proprietary | Single Building | Communications are always encrypted in a HART network. The network uses a 128-bit AES encryption system. The security manager in the WirelessHART gateway administers three parameters: Network ID, Join key and Session key. In addition to individual sessi | Typical HART use cases are process industry monitoring (automotive production process, chemical segments, food and beverage, power generation); process optimization , safety enhancements , environment and health monitoring, maintenance optimization, etc. | “HART” is an acronym for Highway Addressable Remote Transducer. The HART Protocol uses Frequency Shift Keying (FSK) standard to superimpose digital communication signals at a low level on top of the 4-20mA. This enables two-way field communication to take |
| 21 | Z-Wave | Z-wave alliance | http://www.z-wave.com/ | https://z-wavealliance.org/z-wave-specification/ | 915MHz (USA) 868MHz (EU) | 30-100m | 40kbps (915MHz) and 20kbps (868MHz) | Low | Mesh | Yes | Proprietary | Single Building | Z-wave provides packet encryption, integrity protection and device authentication services. End-to-end security is provided on application level (communication using command classes). It has in-band network key exchange and AES symmetric block cipher algo | It is a wireless communications protocol used primarily for home automation. Important Z-wave use cases are smart homes and buildings, smart offices, smart sensors, smart wall switches, smart bulbs, thermostats, windows, locks and security systems, swimm | Z-Wave protocol was developed by Sigma Designs, Inc. and determined by ITU G.9959 recommendation. Like other protocols and systems developed for the home and office automation , a Z-Wave system can be controlled via the Internet from a smart phone, tablet |
| 22 | ZigBee | ZigBee Alliance | http://www.ZigBee.org/ | https://zigbeealliance.org/wp-content/uploads/2019/11/docs-05-3474-21-0csg-zigbee-specification.pdf | 2.4GHz, 915MHz (US), 868 MHz (EU) | 30-100m | 250 kbps (2.4GHz) 40kbps (915MHz) 20kbps (868MHz) | Low | Mesh | Yes | Open | Single Building | ZigBee is considered to be a secure wireless communication protocol, with security architecture built in accordance with IEEE 802.15.4 standard. Security mechanisms include authentication – authorized access to network devices, integrity protection and en | Some representative ZigBee use cases are correlated with smart homes and smart buildings applications, like different smart home gateways, sensors and alarms that are monitoring almost everything - from temperature, humidity, or lighting and movement, sma | ZigBee is wireless PAN (Personal Area Network) technology evolved from IEEE 802.15.4 wireless standard and supported by the ZigBee Alliance. IEEE 802.15.4 standard defines the physical and data link layer with all details about the robust radio communicat |
| 23 | Thread | Thread Group (Google, Samsung, etc.) | https://www.threadgroup.org/ | https://portal.threadgroup.org/DesktopModules/Inventures_Document/FileDownload.aspx?ContentID=3014 | 2.4GHz | ≈ 30m | 250kbps | Low | Mesh | Yes | Open | Single Building | Thread utilizes a network-wide key that is used at the Media Access Layer (MAC) for encryption. This key is used for standard IEEE 802.15.4 authentication and encryption. IEEE 802.15.4 security protects the Thread network from over-the-air attacks origina | Thread provides wireless connectivity for home automation via the control of lights – smart bulbs and outlets, smoke detectors, cameras and other security systems, thermostats, utilities measurements, smart digital locks, hubs and controllers, different | Thread was designed with the Internet’s proven, open standards to create an Internet Protocol version 6 (IPv6) based mesh network, with 6LoWPAN as its foundation. Thread can securely connect up to 250 devices in a wireless mesh network . |
| 24 | DigiMesh | DigiMesh | https://www.digi.com | https://www.digi.com/resources/documentation/digidocs/pdfs/90001506.pdf | 2.4GHz/900 MHz (USA)/868 MHz (EU) | ≈ 100m | 250 kbps (2.4) 40kbps (915) 20kbps (868) | Low | Mesh | Yes | Proprietary | Single Building or WAN | DigiMesh security features are 128-bit AES encryption and 256-bit AES - available on some products, such as XBee3 and XTend. One command (KZ) sets a password that prevents intruders from sending or receiving unsecured remote AT commands. For added securi | Some representative DigiMesh use cases are monitoring in food safety, facility and pharmacy domains, supply chains applicability, transportation and logistics, environmental monitoring etc. | DigiMesh is a proprietary peer-to-peer wireless networking topology developed by Digi International. The protocol allows for time synchronized sleeping nodes/routers and battery powered operations with low-power consumption. |
| 25 | MiWi | Microchip Technology | http://www.microchip.com/ | http://www.microchip.com/design-centers/wireless-connectivity/embedded-wireless/802-15-4/miwi-protocol | 2.4GHz, 700MHz/800MHz/900MHz | ≈ 300m | 20kbps | Low | Mesh or Star | Yes | Proprietary | Single Building | The MiWi protocol follows the MAC security definition specified in IEEE 802.15.4 and is based on 128-bit AES model. MiWi security mechanisms can be categorized into three groups: • AES-CTR mode encrypts MiWi protocol payload. • AES-CBC-MAC mode ensures th | MiWi is designed for low-power, cost-constrained networks, such as industrial monitoring and control, home and building automation, remote control, wireless sensors, lighting control, HVAC systems and automated meter reading. | MiWi uses small, low-power digital radios based on the IEEE 802.15.4 standard. Although the MiWi software can all be downloaded for free from its official website, it is a proprietary solution that requires use only with Microchip microcontrollers. It was |
| 26 | EnOcean | EnOcean | https://www.enocean.com/en/ | https://www.enocean-alliance.org/specifications/ | 902 MHz/928.35 MHz/868.3 MHz/315 MHz | ≈ 30m (outdoor 300m) | 125kbps | "Battery Free" | Mesh | Yes | Proprietary | Single Building | The unique 32-bit identification number (ID) of the standard Enocean modules cannot be changed or copied - it is the protection against duplication. This authentication method already offers field-proven secure and reliable communication in building auto | The EnOcean wireless standard (ISO/ IEC 14543-3-1X) in sub 1GHz is optimized for use in buildings, as a radio range of 30m indoors is possible. Enocean representative use cases are smart lighting, temperature and air quality monitoring, positioning and s | The EnOcean wireless standard is geared to wireless sensors and wireless sensor networks with ultra-low power consumption. It also includes sensor networks that utilize energy harvesting technology to draw energy from their surroundings – for example from |
| 27 | Weightless (W, N, P) | Weightless Special Interest Group | http://www.weightless.org/ | http://www.weightless.org/about/weightless-specification | 138MHz, 433MHz, 470MHz, 780MHz, 868MHz, 915MHz, 923MHz | ≈ 2km (P), 5km (W, N) | ≈ 600bps-100kbps | Low (N), medium (W, P) | Star | Yes | Open | WAN | In Weightless standard AES-128/256 encryption and authentication of both the terminal and the network guarantees integrity whilst temporary device identifiers offer anonymity for maximum security and privacy. OTA security key negotiation or replacement is | Typical Weightless use cases are smart metering, vehicle tracking, asset tracking, smart cars – vehicle diagnostics and upgrades, health monitoring, traffic sensors, smart appliances, rural broadband, smart ePayment infrastructure, industrial machine mon | The Weightless Special Interest Group (SIG) offers three different protocols— Weightless-N, Weightless-W, and Weightless-P. Weightless-W open standard is designed to operate in the TV white space (TVWS) spectrum. Weightless-W represents a model the Neul |
| 28 | mcThings | mcThings | https://www.mcthings.com/ | https://www.mcthings.com/platform/ | 2.4GHz | ≈ 200m | 50kbps | Low | Star | Yes | Proprietary | Single Building | mcThings technology is embedded with 128 bits AES encryption algorithm. | Some representative mcThings use cases are asset tracking, industrial automation, maintenance optimization, location monitoring, security systems (theft and loss prevention), status monitoring, agriculture and food industry automation, environmental moni | mcThings is a good solution for use-cases that have sets of sensors in some urban areas (neighboring buildings). The technology is power efficient and requires minimal maintenance efforts. Network is expandable with bridges, and sensors have long-life bat |
| 29 | LoRa | LoRa Alliance | https://www.lora-alliance.org/ | https://lora-alliance.org/resource-hub/lorawanr-specification-v11 | License-free sub-gigahertz radio frequency bands like 433 MHz, 868 MHz, 915 MHz, 923 MHz . | ≈ 30km | 50kbps | Low | Star | Yes | Open | WAN | Based on security for IEEE 802.15.4 wireless networks, AES encryption with the key exchange is implemented in LoRa. In higher OSI levels built over the LoRa PHY layer, two layers of security are utilized - one for the network and one for the application | Typical LoRa use cases are power metering , water flow, gas or similar quantitative monitoring; logistics and transportation monitoring; smart home, office and smart city appliances; environmental sensing like air pollution, flooding, avalanche, forest f | LoRa provides wireless, low-cost and secure bi-directional communication for Internet of Things (IoT) applications. LoRa is optimized for long range communication, low power consumption and is designed to support large networks deployment. LoRa is built |
| 30 | SIGFOX | SigFox | https://www.sigfox.com/en | https://build.sigfox.com/sigfox-device-radio-specifications | The Sigfox technology globally works within the ranges from 862 to 928 MHz | ≈ 40km | 600bps | Low | Star | Yes | Proprietary | WAN | Security first comes within devices During the manufacturing process, each Sigfox Ready device is provisioned with a symmetrical authentication key. Security is also supported by radio technology. The SigFox technology encryption is designed in collabo | SIGFOX applicability potential is great. Some representative use cases are supply chain & logistics automation, manufacturing automation, smart cities, smart buildings and smart utilities & energy management and monitoring, smart agriculture etc. | SIGFOX protocol is a patented and closed technology. While it's hardware is open, the network however isn’t and customers must be subscribed to it. Note that while there are strict limitations of SIGFOX in terms of throughput and utilization, it is intend |
| 31 | DECT ULE | ETSI | https://www.ulealliance.org/organization | https://www.etsi.org/deliver/etsi_ts/102900_102999/10293901/01.01.01_60/ts_10293901v010101p.pdf | 1880MHz - 1900MHz | ≈ 300m | 1Mbps | Low | Star | Yes | Open | Single building | DECT ULE devices use a combination of general DECT security procedures and ULE specific security procedures. General DECT security procedures are device registration (subscription), device and base authentication, key generation (including keys for ULE us | DECT ULE is new technology developed for different IoT use cases like home, office and industrial automation, control and monitoring systems, medical care and security systems. | DECT Ultra Low Energy (ULE) is a new technology based on DECT and intended for Machine-to-Machine communications such as Home and Industrial automation. DECT ULE standard has advantages of long distance range, no interference and large data rate/bandwidth |
| 32 | Insteon | Smartlabs | https://www.insteon.com/ | https://www.insteon.com/technology#ourtechnology | 915MHz ( USA) 869.85 MHz (EU) 921.00 MHz (Australia) | ≈ 50m | 38400bps - via RF 13165bps - via powerlines | Low or battery free (plug-in) | Mesh | Yes | Propriatary | Single building | Insteon network security is maintained via linking control to ensure that users cannot create links that would allow them to control a neighbors’ Insteon devices, and via encryption within extended Insteon messages for applications such as door locks and | INSTEON is optimized for home and office automation and allows networking of different devices like light switches, thermostats, home audio, remote controls, leak sensors, pumps, motion sensors, alarms, HVAC systems, security sensors or different remote c | INSTEON allows home automation devices to communicate through power lines, radio frequencies or a combination of both. All INSTEON devices are known as peers. This is because any device can transmit, receive, or repeat the messages from other devices. In |
| 33 | RFID | RFID | https://www.iso.org/standard/73599.html (Example) | A number of organizations have set standards for RFID, including the International Organization for Standardization (ISO), the International Electrotechnical Commission (IEC), ASTM International, etc. RFID standards include: ISO 11784/11785, ISO 14223, I | 125 KHz to 134 kHz, 13.56MHz, 433 MHz, 860MHz - 960MHz. | 0.01m-10m (depending on the frequency range) | 4kbps - 640kbps (depending on the active or passive type of device and frequency range). | Low | point to point | Yes | Open | Single building | The implementation of security mechanisms in RFID technology is based on confidentiality, integrity, and availability. Confidentiality is the information protection from unauthorized access. Integrity is related to data protection from modification and de | Radio-Frequency Identification (RFID) is a technology commonly used for identification, status administration and management of different objects. Moreover, this technology is very important for people identification, as it is deployed in the latest biome | Commonly, a RFID system has three main components: RFID tag, RFID reader and RFID application software. RFID tags can be active (with microchip, antenna, sensors and power supply) or passive (without power supply). RFID reader is another hardware componen |
| 34 | WAVIoT (NB-Fi - Narrowband Fidelity) | WAVIoT | https://waviot.com/ | https://www.cnx-software.com/2016/01/20/waviot-lpwan-technology-powers-low-cost-smart-water-and-electricity-meters/ | 315MHz, 433MHz, 470MHz, 868MHz, 915MHz | ≈ 50km | 10-100bps | Low | Star | Yes | Open | WAN | All WAVIoT data is encrypted bidirectionally from the device to the server using an XTEA 256 bit key block cipher. | Typical WAViOT use cases are smart cities, smart buildings, smart metering, utilities monitoring and metering like water, power - electricity, gas, heat, etc. | NB-Fi (Narrowband Fidelity) is a narrow band protocol which communicates on the sub 1GHz ISM sub bands. DBPSK is used as the modulation scheme in the physical layer. WAVIoT gateways can provide -154 dBm of receiver sensitivity, and cover over 1 million no |
| 35 | DASH7 Alliance Protocol (D7A or D7AP) | DASH7 Alliance | https://dash7-alliance.org/ | https://dash7-alliance.org/download-specification/ | 433MHz | ≈ 2km | 167kbps | Low | Star | Yes | Open | WAN | Similarly to 802.15.4, AES-CBC is used for authentication and AES-CCM for authentication and encryption. | Some representative DASH7 use cases are access control, smart energy, location based services, mobile advertising, industry automation, logistics, building access, mobile payments, ticketing, etc. | D7A complies with the ISO/IEC 18000-7 standard. ISO/IEC 18000-7 is an open standard for the license-free 433 MHz ISM band air-interface for wireless communications. The 433 MHz frequency provides D7A with long propagation distance and better penetration. |
| 36 | Wi-SUN | IETF | https://ietf.org/ | https://tools.ietf.org/id/draft-heile-lpwan-wisun-overview-00.html | 470-510MHz, 779-787MHz, 920.5-924.5MHz (China), 863-870MHz, 870-876MHz (EU), 920-928MHz (USA, Canada and Japan) | ≈ 1000m | 300kbps | Low | Star, Mesh | Yes | Open | WAN | The Wi-SUN security is specified by implementation of the x.509 certificate-based, public-key infrastructure to authenticate devices, as well as Advanced Encryption Standard (AES) encryption and message integrity check. Devices protect their digital cr | Some typical Wi-Sun use cases are smart metering, smart cities, smart buildings, industrial automation, environmental sensing, etc. | The term Wi-Sun is the short form of Wireless Smart Utility Network. Wi-Sun technology is a successful derivation of IEEE 802.15.4 wireless standard that supports IPv6 protocol. |
| 37 | Wavenis | Coronis Systems | http://www.coronis.com | http://www-coronis-com.dyn.elster.com/downloads/Wavenis_Data_Sheet_A4_CS5.pdf | 433MHz, 868MHz, 915MHz | ≈ 1000m | 9.6kbps (433 & 868MHz) / 19.2kbps (915MHz) | Low | Tree, Star | Yes | Open | WAN | Wavenis technology is supported by 128-bit AES encryption. | Some Wavenis use cases are different metering solutions (gas, electricity, water, etc.) applicable to environmental monitoring, smart cities, utilities companies etc. | Wavenis is a wireless technology created by Coronis in the year 2000. It is developed for ultra low power and long range Wireless Sensor Networks(WSNs). It has become popular due to promotion by Wavenis Open Standard Alliance. |
| 38 | MiOTY | Fraunhofer Institute for Integrated Circuits & BTI Ltd. Toronto | https://www.iis.fraunhofer.de/en/pr/2018/20181016_LV_Mioty.html | https://behrtech.com/mioty/ | 915Mhz (USA),868Mhz (EU) | ≈ 20km | 407 bps | Low | Star | Yes | Open | WAN | MiOTY technology implements 128-bit AES encryption. | Some MiOTY use cases are optimized maintenance models, inventory optimization for parts, asset management and tracking, condition and environmental monitoring, smart metering, augmented reality innovative applications, product R&D, improved customer suppo | MIOTY is a low-power, wide-area network (LPWAN) protocol that is purpose-built for massive industrial and commercial IoT deployments. Fraunhofer’s patented Telegram Splitting – the core of the MIOTY protocol, is designed to provide the scalability and ov |
| Wireless technology / standard | Organization that manages the technology / standard | URL of the organization | URL of the standard specification | Frequency | Approximate Range | Data Rate | Power Draw | Topology | Requires hub or gateway | Proprietary or Open | Intended Use | Security | Common use | Comments |
Marin Ivezic
For over 30 years, Marin Ivezic has been protecting critical infrastructure and financial services against cyber, financial crime and regulatory risks posed by complex and emerging technologies.
He held multiple interim CISO and technology leadership roles in Global 2000 companies.