-
5G & Massive IoT Business

The Open RAN Lexicon You Need
The telecoms and digital technologies sectors are notoriously jargonised. Eavesdrop on any conversation at an industry conference (remember those?) and…
Read More » -
5G & Massive IoT Business

Open RAN May Be the Future of 5G, but Can We Keep It Secure?
It’s been a year of contradictions for the telecommunications industry. Like most sectors, it has been heavily impacted by the…
Read More » -
5G Technology

5G in Manufacturing – 5G and Time Sensitive Networking (TSN) for Industrial Automation
In the recent report by IHS Markit – “The 5G Economy – How 5G will contribute to the global economy”…
Read More » -
Cyber-Kinetic Security

Cybersecurity and Safety in the 5G-Enabled Smart-Everything World
Neil Harbisson calls himself a cyborg. Without the antenna implanted in his skull, he would not be able to see…
Read More » -
5G Technology
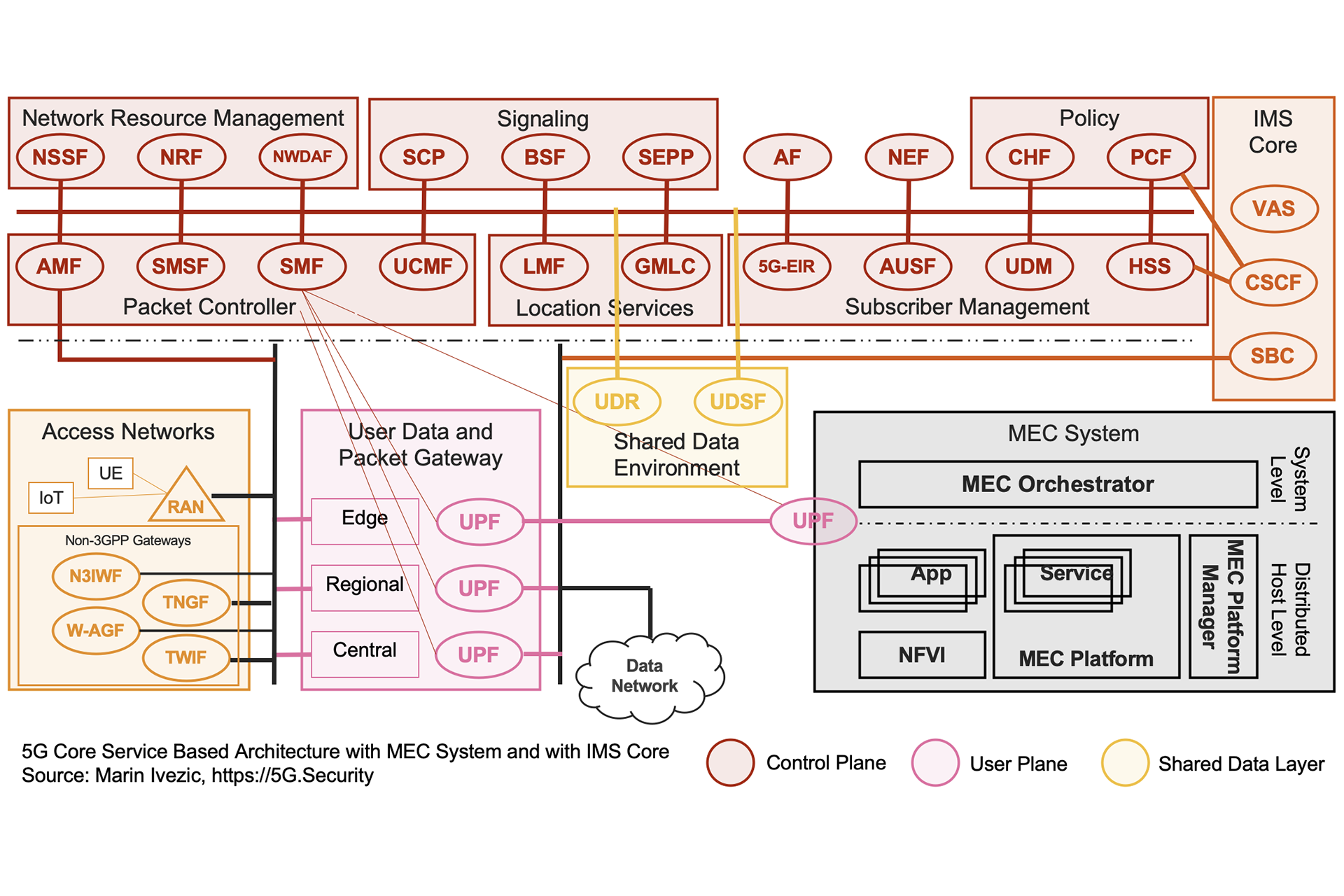
Introduction to 5G Core Service-Based Architecture (SBA) Components
The interest in 5G and mIoT is exploding. It’s exciting to see so many IT and cybersecurity professionals in my…
Read More » -
Smart Cities

Smart Home / Smart Building Connectivity Options and Their Cybersecurity
In a recent session on smart building cybersecurity, a student cheekily asked me “How did we ever connect anything before…
Read More » -
5G & Massive IoT Business
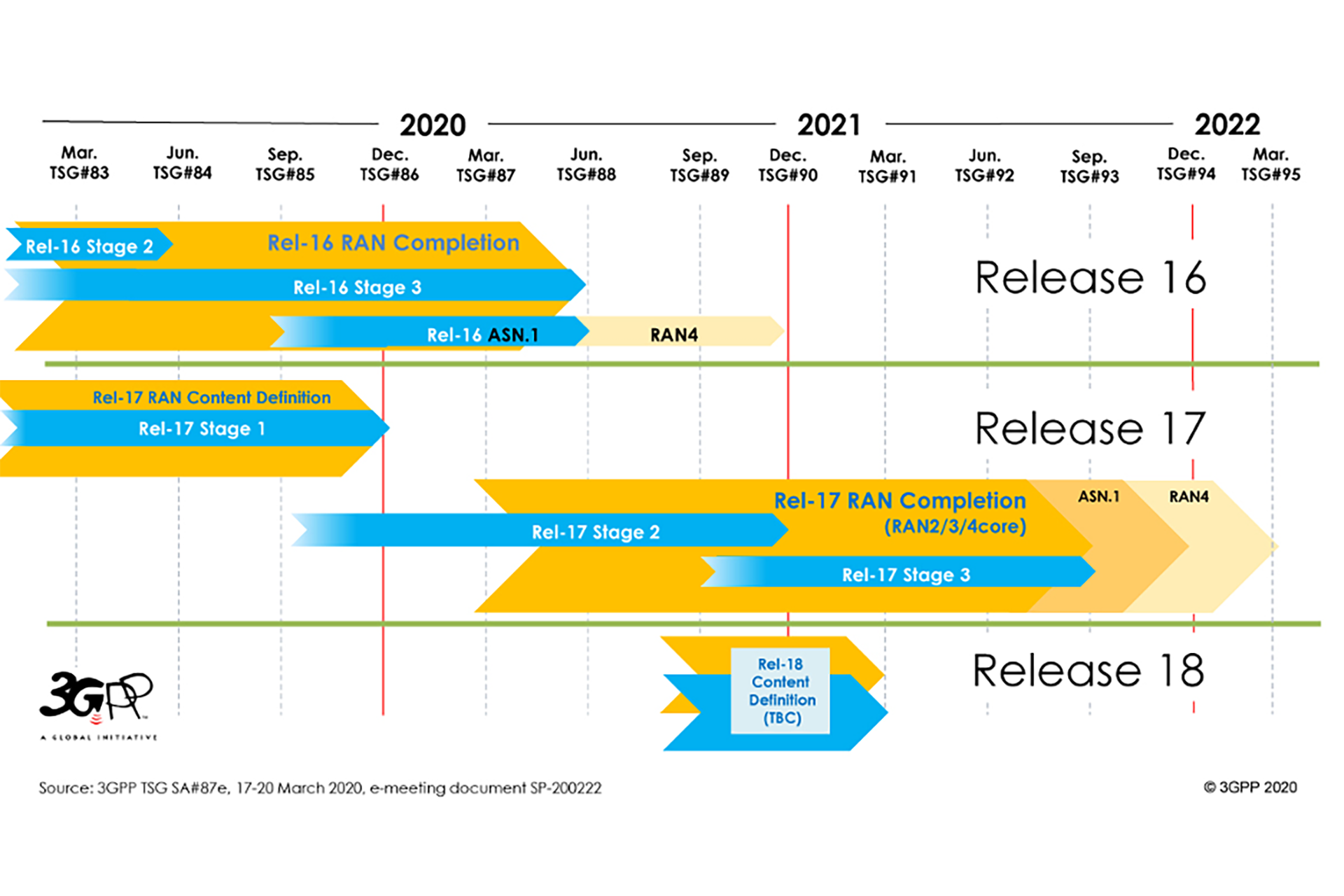
Introduction to 3GPP and 3GPP 5G Releases 15, 16 and 17
In a major milestone for 5G, 3GPP finalized the Release 16 in July – its second set of specifications for…
Read More » -
5G Security

Does the positive review of Huawei UDG source code quality mean that Huawei 5G is secure and reliable?
No, no it doesn’t. Huawei’s code might as well be extremely secure. Their code is certainly the most scrutinized. But…
Read More » -
IoT Networks

IoT Wireless Protocols – Speed & Range – Spreadsheet
IoT Wireless Protocols data rate and range comparison in a spreadsheet format. Includes downloadable Excel spreadsheet.
Read More » -
IoT Networks

IoT Wireless Protocols – Spreadsheet
IoT Wireless Protocols in a spreadsheet format. Includes downloadable Excel spreadsheet.
Read More » -
5G Security News

U.S. lawmakers introduce bill targeting Huawei for industrial espionage
A bipartisan group of U.S. lawmakers today introduced in Senate a bill aimed “To impose sanctions with respect to foreign…
Read More » -
5G Security News

Bell Canada to pause 5G launch due to COVID-19
On Bell’s BCE Inc (BCE) Q1 2020 Results Conference Call on Thursday new Bell’s President and CEO Mirko Bibic said:…
Read More » -
5G Security News

TeraGo commences 5G fixed wireless technical trials in Toronto
TeraGo Inc. (“TeraGo” or the “Company”) (TSX: TGO, www.terago.ca) is a Canadian managed cloud and connectivity solutions company. It owns…
Read More » -
5G & Massive IoT Business

Will Telcos Lose the Edge Computing Battle as Well?
For many end-users of today’s communications technology, the cloud is a somewhat mystical concept, a digital equivalent of aether. Most…
Read More » -
Society 5.0

What COVID-19 Taught Us About the Need for 5G
There are many adjectives that could be used to describe the global outbreak of COVID-19, but perhaps the simplest might…
Read More »