-
Cyber-Kinetic Security
When Hackers Threaten your Life – Cyber-Kinetic Attacks Intro
The attacker stepped out from behind a hedge in the upper-class suburban neighborhood, being careful to stay in the shadows. Across the street, the last lights shining through the windows of the house had just flickered out. She tugged the bottom of her black hoodie into place and pulled the hood up over her head, casting her face deeper in shadow. Her target sat in the driveway at the front of the house, a bright…
Read More » -
Cyber-Kinetic Security
Defeating 21st Century Pirates: the Maritime Cyberattacks
The maritime industry faces a not-so-distant future when ships will be completely autonomous, using navigation data that they receive to plot their own courses with only minimal input from shoreside control centers. The efficiencies this could bring are massive, but before this happens, cybersecurity issues must be addressed. Not only are many vessels configured in ways that invite cyberattacks, but security practices also need to be improved before the industry can safely navigate its future.…
Read More » -
5G Security
Regulating the Security of the Internet of Things (IoT) in a 5G World
In one of those strange inversions of reason, The Internet of Things (IoT) arguably began before the Internet itself. In 1980, a thirsty graduate in Carnegie Mellon University’s computer science department, David Nichols, eventually grew tired of hiking to the local Coca Cola vending machine only to find it empty or stocked entirely with warm cola. So, Nichols connected the machine to a network and wrote a program that updated his colleagues and him on…
Read More » -
Cyber-Kinetic Security
Tangible Threat of Cyber-Kinetic Attacks
Connecting physical objects and processes to the cyber world offers us capabilities that exponentially exceed the expectations of science fiction writers and futurists of past generations. But it also introduces disquieting possibilities. Those possibilities reach beyond cyberspace to threaten the physical world in which we live and – potentially – our own physical well-being. That’s the threat of cyber-kinetic attacks. Our physical world is becoming more connected – which makes it more dependent on the…
Read More » -
Cyber-Kinetic Security
Stuxnet and the Birth of Cyber-Kinetic Weapons
Stuxnet was the first true cyber-kinetic weapon, designed to cripple the Iranian – and perhaps also the North Korean – nuclear weapon programs. It succeeded in slowing the Iranian program, although it was discovered before it could deal the program a fatal blow. Its significance goes far beyond what it did. It marks a clear turning point in the military history and cybersecurity. Its developers hoped for a weapon that could destroy strategic targets without…
Read More » -
Cyber-Kinetic Security
Navigating a Safe Course Through Maritime Cyberattacks
The open seas have long attracted those who yearned for adventure. The risk of pitting oneself against a vast and unforgiving sea has tested sailors’ mettle for millennia. It’s not surprising that the maritime industry is one that thrives on facing – and overcoming – risks. But, as technology increasingly dominates it, growing risks exist that the industry dare not ignore. Its growing effort to increase efficiencies through digitization and automation has made it an…
Read More » -
Cyber-Kinetic Security
Our Smart Future and the Threat of Cyber-Kinetic Attacks
A growing number of today’s entertainment options show protagonists battling cyber-attacks that target the systems at the heart of our critical infrastructure whose failure would cripple modern society. It’s easy to watch such shows and pass off their plots as something that could never happen. The chilling reality is that those plots are often based on real cyber-kinetic threats that either have already happened, are already possible, or are dangerously close to becoming reality. Cyberattacks…
Read More » -
Cyber-Kinetic Security
History of Cyber-Kinetic Incidents and Research
The fact that cyber-kinetic attacks rarely appear on mainstream news doesn’t mean they don’t happen. They happen more frequently than you would think. Many, for various reasons, aren’t even reported to agencies charged with combatting them. This hinders security experts in understanding the full scope and recognizing the trends in this growing problem. We’ll highlight examples of cyber-kinetic incidents and attacks in this chapter. Some were malfunctions that, nonetheless, demonstrated cyber-physical system vulnerabilities. Some were…
Read More » -
RESOURCES
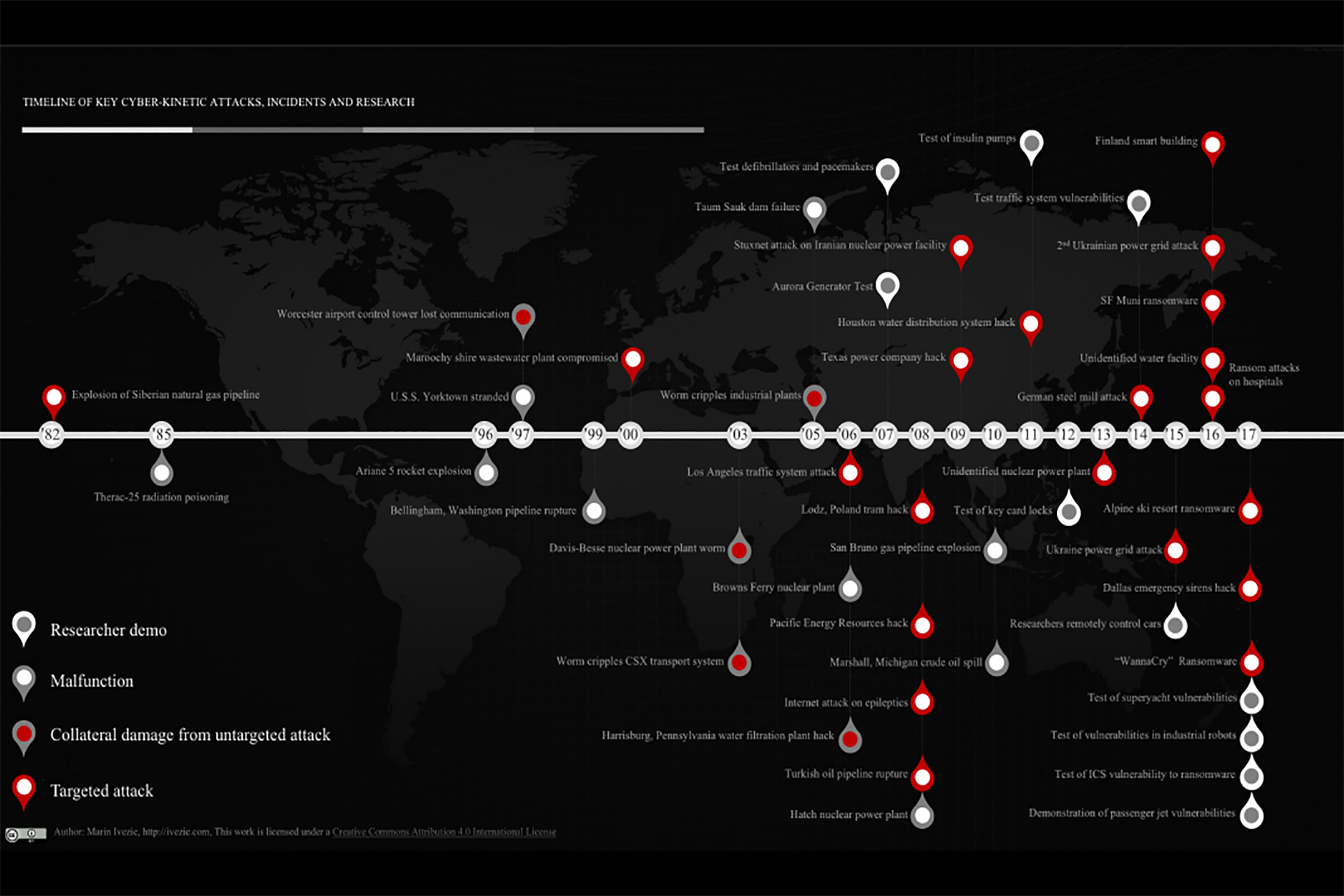
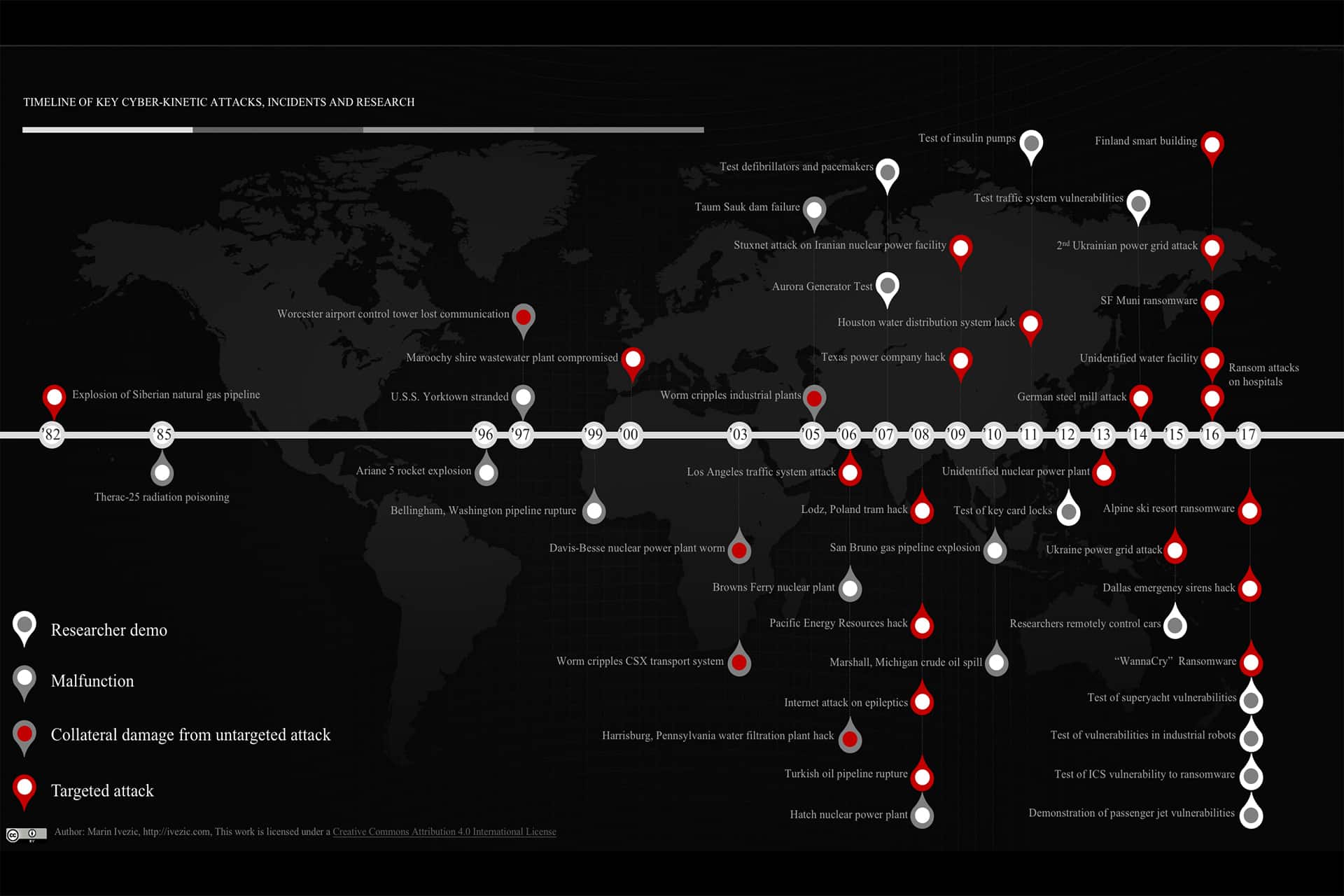
Timeline of Key Cyber-Kinetic Attacks, Incidents & Research
Below is a timeline of key historic cyber-kinetic attacks, system malfunctions and key researcher demos targeting cyber-physical systems (CPS), Internet of Things (IoT) and Industrial Control Systems (ICS) resulting in kinetic impacts in the physical world. I tried to select only those that were first-of-the-kind or that significantly increased general awareness about a particular type of an attack or incident I know that the list is incomplete. That’s where you come in. If you are…
Read More » -
Cyber-Kinetic Security
When Hackers Threaten your Life – Cyber-Kinetic Risks
The attacker stepped out from behind a hedge in the upper-class suburban neighborhood, being careful to stay in the shadows. Across the street, the last lights shining through the windows of the house had just flickered out. She tugged the bottom of her black hoodie into place and pulled the hood up over her head, casting her face deeper in shadow. Her target sat in the driveway at the front of the house, a bright…
Read More »