NSA and CISA Release Part II of Guidance on Securing 5G Cloud Infrastructures

Share via:
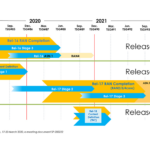
The US National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) recently released the first of a four part series titled Security Guidance for 5G Cloud Infrastructures. This series of four action-oriented documents is intended to provide guidance on how to move toward zero trust in support of securing 5G. It’s been created as a joint industry and government effort with the support of several large contributors through the NSA’s Enduring Security Framework (ESF).
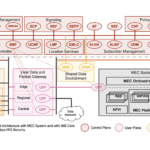
This second release in the series is titled Security Guidance for 5G Cloud Infrastructures – Part II: Securely Isolate Network Resources [PDF] with the focus on ensuring that there is secure isolation among customer resources with emphasis on securing the container stack that supports the running of virtual network functions.
The guidance focuses on “pods” isolated environments used to execute 5G network functions in a 5G container-centric or hybrid container/virtual network function design and deployment and it describes several aspects of Pod security including:
- Strengthening Pod isolation, such as limiting permissions on deployed containers;
- Cryptographically isolating critical Pods using trusted execution environments;
- Using best practices to avoid resource contention & DOS attacks;
- Implementing container image security through build processes, scanning, and
enhancements to the trust environment; and - Implementing real-time threat detection through minimizing noise, curating baseline
behavior, and alerting on anomalous activity.
For more information see the release on the CISA website: https://www.cisa.gov/uscert/ncas/current-activity/2021/11/19/nsa-and-cisa-release-guidance-securing-5g-cloud-infrastructures
The guidance is available here [PDF]: Security Guidance for 5G Cloud Infrastructures – Part II: Securely Isolate Network Resources
All the guidance papers and other useful information will be available at the CISA’s 5G Security and Resilience page or at the NSA’s Enduring Security Framework (ESF) page.
Marin Ivezic
For over 30 years, Marin Ivezic has been protecting critical infrastructure and financial services against cyber, financial crime and regulatory risks posed by complex and emerging technologies.
He held multiple interim CISO and technology leadership roles in Global 2000 companies.
-
Marin Ivezic#molongui-disabled-link
-
Marin Ivezic#molongui-disabled-link
-
Marin Ivezic#molongui-disabled-link
-
Marin Ivezic#molongui-disabled-link
-
Marin Ivezic#molongui-disabled-linkNovember 17, 2022
-
Marin Ivezic#molongui-disabled-linkSeptember 20, 2022
-
Marin Ivezic#molongui-disabled-link
-
Marin Ivezic#molongui-disabled-linkApril 27, 2022
-
Marin Ivezic#molongui-disabled-link
-
Marin Ivezic#molongui-disabled-linkMarch 25, 2022
-
Marin Ivezic#molongui-disabled-linkFebruary 8, 2022
-
Marin Ivezic#molongui-disabled-linkFebruary 4, 2022
-
Marin Ivezic#molongui-disabled-link
-
Marin Ivezic#molongui-disabled-link
-
Marin Ivezic#molongui-disabled-link
-
Marin Ivezic#molongui-disabled-link
-
Marin Ivezic#molongui-disabled-link
-
Marin Ivezic#molongui-disabled-link
-
Marin Ivezic#molongui-disabled-link
-
Marin Ivezic#molongui-disabled-linkFebruary 28, 2021
-
Marin Ivezic#molongui-disabled-linkFebruary 24, 2021
-
Marin Ivezic#molongui-disabled-linkFebruary 21, 2021
-
Marin Ivezic#molongui-disabled-linkJanuary 20, 2021
-
Marin Ivezic#molongui-disabled-linkNovember 27, 2020
-
Marin Ivezic#molongui-disabled-link
-
Marin Ivezic#molongui-disabled-linkSeptember 27, 2020
-
Marin Ivezic#molongui-disabled-link
-
Marin Ivezic#molongui-disabled-link
-
Marin Ivezic#molongui-disabled-link
-
Marin Ivezic#molongui-disabled-link
-
Marin Ivezic#molongui-disabled-linkMay 16, 2020
-
Marin Ivezic#molongui-disabled-link