IIoT and Trust and Convenience: A Potentially Deadly Combination

When microwave ovens first arrived on the market in 1967 they were met with public skepticism. Perhaps it was because, not long before, the same technology now promising to safely cook consumers’ evening meals was the backbone of a military radar. Perhaps it was the $495 price tag (more than $3,700 in today’s money).
Whatever the reason, in the early 1970s the percentage of Americans owning a microwave was tiny. By 2011, it was 97%. What changed?
Trust and convenience.
When microwave technology was first released, it was difficult to trust. Cooking without using heat? It was simply too alien. In 1973, Consumers Union stated that microwave ovens couldn’t be considered safe because there was no solid data on safe levels of radiation emission.
In a 1974 New York Times interview, Leonard Smiley, Consumers Union’s appliance division chief declared, “We see no reason to change our minds, but we are always open to changing it when additional data comes in.”
And that’s what happened between 1974 and today – data convinced consumers that the technology could be trusted. At the same time, the public was motivated by the incredible convenience that the microwave oven offered.
Today, that hunger for convenience is driving the exponential growth of the internet of things (IoT) and the almost unquestioning adoption of this technology among consumers. This time, however, it is not matched with trust. A 2017 Cisco study found that, while 53% of respondents felt that IoT devices made their lives more convenient, only 9% trusted the tech.
Astonishingly, though, despite this lack of trust almost half of survey participants said they were not willing to disconnect from their IoT equipment and services. They were prepared to take the risk. Because IoT devices were already so integrated into their lives that they couldn’t imagine parting with them.
There is something unsettling in the paradox of low trust and high attachment. It runs counter to all our better instincts. When people admit that they don’t trust technology but refuse to do without it, they are complicit in willful denial.
What makes the Cisco research even more perturbing is that the ‘risk’ that the survey respondents referred to was a danger to privacy and personal data. Of course, those are legitimate concerns, but in the multi-vector landscape of IoT, there are far bigger threats than stolen identity.
Let’s get physical with IIoT
One of the reasons the IoT habit is so hard to kick is that these devices have a physical impact on our world. They take the digital and make it manifest in functional tools that we experience as lights that dim at the sound of our voice, watches that tell us our heart rate is too high, fridges that tell us we’re out of milk, or cars that warn us of other vehicles.
These are cyber-physical systems (CPSs). They cross the threshold between the digital world and the physical one, which is what makes them so useful to those seeking greater convenience.
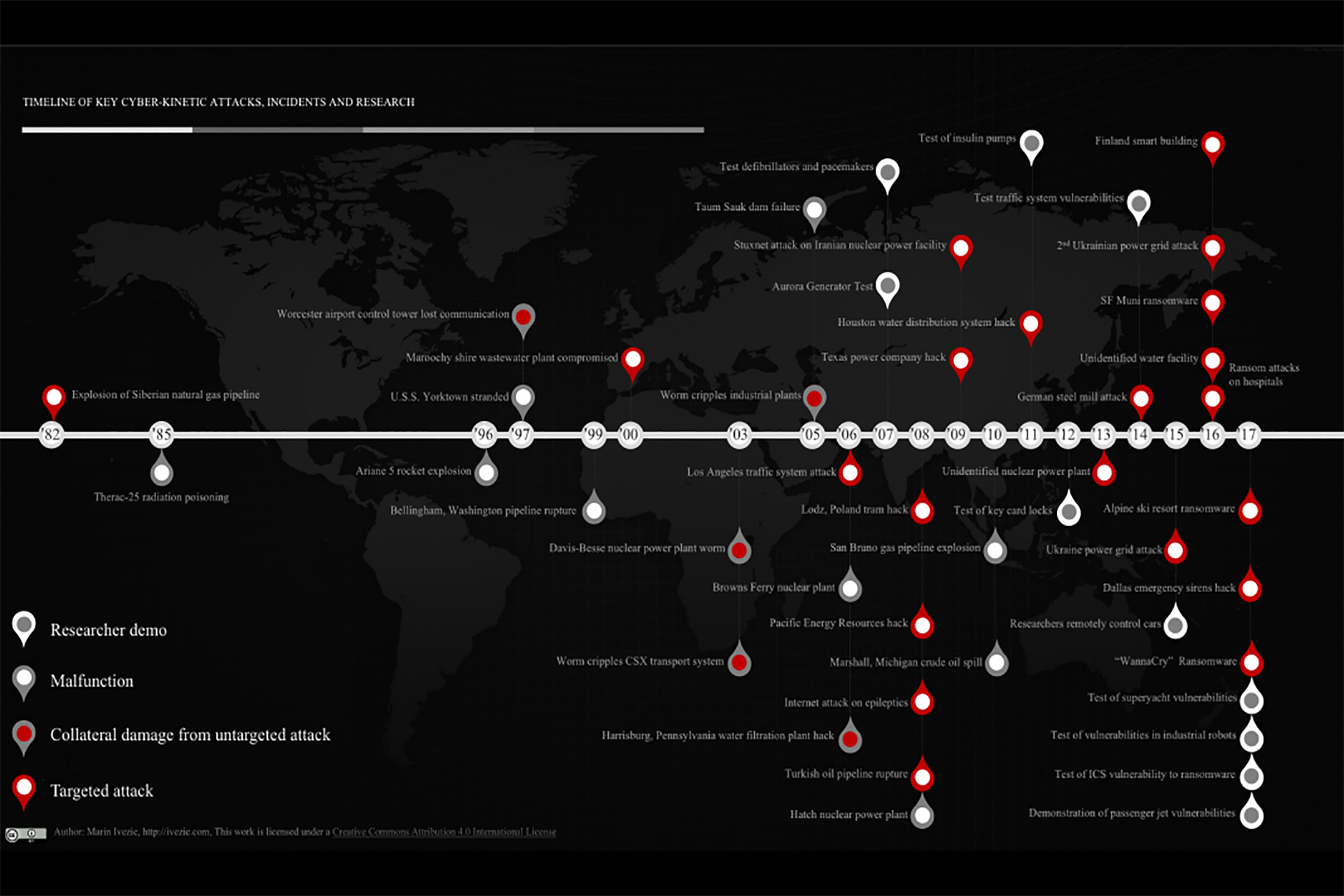
But it is also what makes them so potentially dangerous. CPSs have the potential to affect their surroundings, but unlike strictly mechanical systems they also have the potential to be hacked. Those that control the cyber can then control the physical, with possibly lethal consequences.
As far back as 2015, Charlie Miller, a security researcher at Twitter, and Chris Valasek, director of Vehicle Security Research at IOActive, proved the havoc that could be wreaked by hackers commandeering CPSs. In a now-famous exercise for Wired magazine, the duo used remote access to hack into a car driving on the highway. From 10 miles away they were able to control the vehicle’s air conditioning, radio, windscreen wipers. But they were also able to cut the engine and take over the steering.
Now imagine the same scenario extrapolated across a network of driverless cars traveling at over 100 miles an hour in perfect precision. The damage that could be done in an instant by cyber attackers who infiltrate the network, or even just one car, is harrowing to consider. That is the nature of cyber-kinetic risk.
The Mirai distributed denial of service (DDoS) attack of 2016, which brought down internet connectivity across a large part of the US east coast, is an early example of how IoT devices may be used to significantly impact public well-being. It’s not hard to predict some of the damage that could be done in smart cities where water, waste and critical services rely on effective cyber systems.
However, the major weight of IoT cyber-kinetic risk rests outside the consumer product domain. The industrial internet of things (IIoT) is growing quickly as more and more companies seek to access the business value of connected devices and systems in industries as diverse as mining, manufacturing, and energy.
Marx and the machines and the IIoT
German philosopher-economist Karl Marx famously pointed to ownership of the means of production as the primary cause of stratification in society. The wealthy, independent bourgeoisie, he said, own the means of production while the proletariat work to keep those institutions operating profitably.
Marx believed that this distinction between the classes leads to progressive deterioration of living and working conditions for the proletariat, with revolution being the inevitable result. Today, there certainly is a revolution underway in the way goods are produced, but it has less and less to do with the worker.
When people talk about the internet of things they are almost always referring to gadgets and electronic products. They are talking about smart watches, smart phones, smart homes, smart meters, even smart toys. It seldom occurs to people, however, that all of these products are produced somewhere, and that those production processes themselves are being redefined by the IIoT.
Smart robotics, intelligent warehousing, remote AR-driven management of industrial machinery, self-driving trucks and tractors – the footprint of IIoT devices and technology in primary and manufacturing industries is growing rapidly. Companies have moved beyond automation to leverage the profound business value of real-time connectivity.
Entire factories of robots talking to each other via the cloud are able to build a car every 77 seconds. Shipping companies use IIoT chips and sensors to constantly optimize transport routes and delivery schedules, soon to be carried out by autonomous ships. IIoT-linked wearables are used to keep workers safe by, for example, using real-time biometric data to help avoid workplace fatigue and preempt accidents.
There is some irony in this. Though the IIoT can legitimately contribute to better health, safety, and environment (HS&E), without sufficient attention paid to security it could also turn out to be the single biggest risk to HS&E and human life.
The devil in the detail
Accenture estimates that the IIoT could add $14.2 trillion to the global economy by 2030. Businesses are eager to claim their slice of this cyber-physical pie. Through better efficiencies, greater economies of scale, higher outputs, and lower OPEX the IIoT will change the fabric of the industrial world.
The key to this potential success is interoperability. According to McKinsey, interoperability – the ability of systems or elements of systems to function harmoniously and in unison – is required for 40 percent of potential value across IoT applications, nearly 60 percent in some settings.
This makes intuitive sense. The IoT is an ecosystem, a cyber-kinetic network of chips, sensors, devices, software, communication services, all working together digitally to make physical things happen. No single technology can provide a total solution. With so many devices produced by many different manufacturers from many different countries representing many different regulatory perspectives, just getting the various nodes in an IIoT network to talk to each other is an achievement.
Getting them to do so safely is another matter entirely.
Many industrial organizations are embarking on massive digitization campaigns without knowing how to secure IIoT. In the race for a competitive advantage they are proceeding quickly, sometimes rashly and without sufficient prudence. Most companies are familiar with, and pay close attention to, the due diligence required to satisfy compliance regulations. However, regulatory specifications for IIoT are still in their infancy.
Without these frameworks, companies are often not motivated to ensure that their IIoT systems are secure against cyber attacks. Often they assume or hope that device vendors have paid enough attention to cybersecurity, but this is rarely the case. In an intensely competitive market, most vendors are focused on getting their products in front of potential clients as quickly as possible. Cybersecurity is usually an afterthought or, even if attention is paid to security through the device’s design and manufacturing, most producers do not have expert cybersecurity knowledge. Even with the best intentions, their security systems prove to be insufficient.
The results of cyber attacks on IIoT could be catastrophic. First, there is the immediate concern for the safety of workers and employees on the industrial front lines. When ships, trucks, machines, entire processing plants or even personal equipment can be hijacked with malicious intent, the physical danger to humans is high.
Then there is a broader concern: industrial systems are at the heart of primary infrastructural networks like energy grids and rail, road or marine transport. The massive scale of devices that will make up these networks as IIoT comes more online means that the number of attack vectors becomes almost unmanageable. Each of these vectors is a potential gateway into the wider network – bring any of those major systems down and a country can be brought to its knees.
There are, however, steps that can be taken:
Practice better cyber hygiene
This seems obvious – any business not already prioritizing cybersecurity is unlikely to survive the 21st Century – but it needs to be emphasized. The landscape of cyber threats is moving constantly and quickly. The technology being targeted and the technology being used for targeting are evolving exponentially. Staying on top of this is not a once-off or annual review process. Businesses need to be constantly refining their processes, procedures, and protocols.
Understand IIoT and HS&E
As evidenced by a recent announcement by Business Roundtable, the purpose of corporate business is being redefined by shifts in public and private expectations. Shareholder primacy is no longer the number one consideration, all stakeholders need to be considered in the purpose and operation of business, including customers, employees, suppliers, communities and shareholders.
Now more than ever businesses have a duty of protection to their employees and those that their business activities impact. For industrial companies, there is an additional responsibility in the emergent risks posed by IIoT. As these organizations move into greater IoT enablement, it is critical that they work with HS&E and cybersecurity professionals jointly to interpret and plan for imminent threats. This is a new territory and very few businesses are equipped to navigate it alone.
Engage government and regulators
In IIoT companies are often working with devices that have been manufactured in one country (sometimes several), sold in another, and used in yet another. In addition, the software and telecommunications service providers that give life to these devices are also distributed across the globe. Though some international standards exist, there is insufficient alignment in policy and regulation to ensure that IIoT cybersecurity is enforced.
Governments and regulators need to work more strategically in developing cross-border and cross-industry frameworks to manage IIoT’s inherent danger to the public. Business, however, needs to be more proactive in this regard. Rather than seeing policy something that is applied to them, organizations need to see it as a co-creative process. Only by combining the experience and expertise of regulators, cybersecurity experts, and the companies that are dealing with these issues on a daily basis can we hope to devise effective policies and regulations.
Assign end-to-end accountability
Any large-scale industrial digitization project requires the participation of multiple role players, including the buyer, a large number of different IoT vendors, systems integrators and software developers, process change specialists. It is a long chain and the more links there are the greater the potential for cyber insecurities to manifest.
One of the easiest and most impactful things a buyer can do to limit exposure to cyber risk is to make one party accountable for end-to-end cybersecurity implementation and management. This may be the buyer itself, a systems integrator or a cybersecurity specialist, but having a holistic view of the operation and its parts is critical to effective threat management.
The biggest mistake I see with my clients is that no one is accountable for cybersecurity because everyone assumes that someone else will do it. And they don’t want to take on that responsibility. It is more convenient to ‘trust’ that the problem is taken care of, though it seldom is.
Cyber vulnerabilities most often happen in gaps between accountabilities.
Marin Ivezic
For over 30 years, Marin Ivezic has been protecting critical infrastructure and financial services against cyber, financial crime and regulatory risks posed by complex and emerging technologies.
He held multiple interim CISO and technology leadership roles in Global 2000 companies.